![]()
![]()
Hello and you're very well welcomed to this separate page of PC Helper Laboratory !!!
I decided to review a totally new product just launched by Kaspersky Labs - Kaspersky Anti-Hacker.
Program/Utility: Anti-Hacker
Version/Build: 1.0.62.0
Author: Eugene Kaspersky Labs
Vendor(s): Eugene Kaspersky Labs, ZDNET
Author's Webpage: http://www.kasperskylabs.com
Program's Webpage: == Not available ==
Download page/Direct Download Link:
ftp://downloads1.kaspersky-labs.com/trial/KAntiHacker/kantihacker_eng_trial1m.exe
Shareware Limitations: limited time of usage (1 month)
![]()
[min. - 1.0 ; max. - 10.0]
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Kaspersky® Anti-Hacker is the personal firewall, which provides full-scale protection for PC, running Windows, from all the attempts of non-authorized access to data, as well as from the hacker attacks both from Internet and Intranet.
Full-scale control over the network activity
Kaspersky® Anti-Hacker provides control over the computer activity on the base of two-level analysis of system network activity.
![]() Tracking activity of
Internet-connected applications (high -level operations).
Integrated analysis of activity of such Internet- connected applications like
Web-browsers, mail applications, file transfer application, etc.
Tracking activity of
Internet-connected applications (high -level operations).
Integrated analysis of activity of such Internet- connected applications like
Web-browsers, mail applications, file transfer application, etc.
![]() Packet filtration of incoming and outgoing
data (low-level operations). At this level
Kaspersky® Anti-Hacker analyses directly the packets, sent or received by
computer.
Packet filtration of incoming and outgoing
data (low-level operations). At this level
Kaspersky® Anti-Hacker analyses directly the packets, sent or received by
computer.
Filtration rules setting
According to the user tasks software allows for creation or changing any set of rules for the tracking of applications activity as well as for packet filtration.
Ability to set up special security rules for the internet-connected applications can be represented in Internet access to be allowed or denied for the particular application depending on its type - mail client, internet-pager, web-browser, etc., or to allow specific type for activity for each concrete application (i.e. to set remote services and addresses with whose the application can interact).
On
setting packet filtration rules, it's possible to allow or to deny transferring
data of specific types. The decision on the following actions with the packet is
taken on the base of analysis of the information stored in the packet header:
sender or recipient's IP-address, data transfer protocol to be used, etc. This
type of rules can be applied to all applications. Packet filtration also
provides effective protection against hacker attacks.
At this time Kaspersky Anti-Hacker is not compatible with ADSL modems.
Customized security levels
Depending on your tasks, Kaspersky® Anti-Hacker allows for making choice among the five security levels starting with complete protection turn-off up to total block of all Internet connections, for each of whose levels you can specify security and packet filtration rules.
Efficient protection against known types of hacker attacks
Kaspersky® Anti-Hacker partly functions in automatic mode. Attack Detector provides reliable defense against such known types of hacker attacks like port scanning, ping, etc.
On choosing some security levels you can also use additional security tool - Stealth mode. Thanks to SmartStealth technology it becomes more difficult to detect your computer from outside. In this mode any network activity is prohibited if not explicitly allowed by the user rules. This mode allows for successful prevention of hacker attacks including DoS (Denial of Service), while having no negative influence on the user performance.
Automatic self-learning system
Kaspersky® Anti-Hacker contains an ability to expand the list of security roles for Internet-connected application with the self-learning function. If an event occurs which is not described by the predefined rules, you can add the method of its handling to the list. In this way you can create security profile, which will ideally meet your requirements.
Check for integrity of executable files
Kaspersky® Anti-Hacker provides applications protection from the unauthorized attempts to substitute their original executable files. If this kind of substitution detected there is an option to Block any further network activity of this application, due to all other rules in this list will be disabled; or to continue to trust to this application without making any changes in its rules. Check for executable files integrity is performed on the on the base of CRC sums, first calculated on file appearance in the system, and further periodic checking of their value.
![]()
1) Security Level
Security Level is a basic option that can be set directly from the main window of the program. There is nothing actually new to explain because all the descriptions are available in Anti-Hacker (one of them is illustrated by the screenshot). Just remember the following when choosing the level:
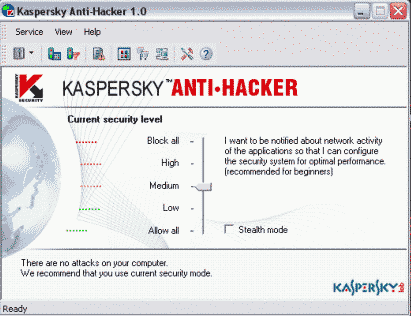
![]() 'Allow All' Mode actually disables Anti-Hacker because it
allows any kind of access for any kind of application in the Internet or on your
computer. Use it when you know what the application activity is about but you
need it for some purposes but it's disallowed by Anti-Hacker due to some
reasons. This usually makes your computer sensitive to virus and Windows
attacks, hackers and Internet Trojans.
'Allow All' Mode actually disables Anti-Hacker because it
allows any kind of access for any kind of application in the Internet or on your
computer. Use it when you know what the application activity is about but you
need it for some purposes but it's disallowed by Anti-Hacker due to some
reasons. This usually makes your computer sensitive to virus and Windows
attacks, hackers and Internet Trojans.
![]() 'Block All' Mode
disables any Internet functionality of any kind of application on your computer.
Use it when you definitely know that something's wrong with your PC and it's
dealing with the Internet.
'Block All' Mode
disables any Internet functionality of any kind of application on your computer.
Use it when you definitely know that something's wrong with your PC and it's
dealing with the Internet.
![]() 'Low' Mode is
used for Internet-only protection. Use it if you "believe" all applications
running on your PC and want to be protected only from hackers and Internet
attacks.
'Low' Mode is
used for Internet-only protection. Use it if you "believe" all applications
running on your PC and want to be protected only from hackers and Internet
attacks.
![]() 'High' Mode
blocks ALL applications, EXCEPT for the ones specified by you in application
rules (reviewed below on this page). Use it when your system is already set up
and you don't need to configure Anti-Hacker. It doesn't allow to reconcile
Anti-Hacker with any new applications that you didn't know but would like to
configure, for example.
'High' Mode
blocks ALL applications, EXCEPT for the ones specified by you in application
rules (reviewed below on this page). Use it when your system is already set up
and you don't need to configure Anti-Hacker. It doesn't allow to reconcile
Anti-Hacker with any new applications that you didn't know but would like to
configure, for example.
![]() 'Medium' Mode is
the most neutral. That's what you start with when using Anti-Hacker and is
recommended to use. It provides abilities to configure Anti-Hacker and can be
called "asking" mode because for each new Anti-Hacker action or activity it asks
you what to do - Block, Allow, etc. or Customize the action as a rule for the
future. I would recommend to use this as well. You will also be informed about
any activity of any application and given control of it.
'Medium' Mode is
the most neutral. That's what you start with when using Anti-Hacker and is
recommended to use. It provides abilities to configure Anti-Hacker and can be
called "asking" mode because for each new Anti-Hacker action or activity it asks
you what to do - Block, Allow, etc. or Customize the action as a rule for the
future. I would recommend to use this as well. You will also be informed about
any activity of any application and given control of it.
2) Application rules
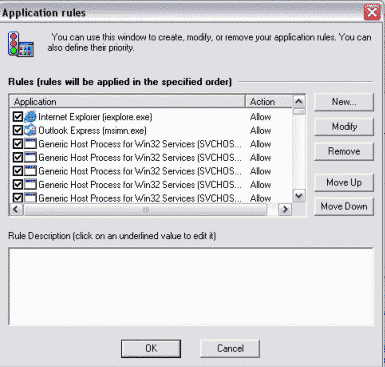
This is a second important option. If you use "Medium" Security Level Mode you won't actually open it often. This is for configuring application access manually. Here you can either manage rules already created by Anti-Hacker (with your confirmation) or add new rules. When adding a new rule it's possible for you to:
![]() Allow activity of application according to its type.
This rule allows application (you specify it's name) to work strictly according
to its type (you specify it's type). For example, you have a program 'A'
installed on your PC and it's an FTP Client. But somehow it's been infected by a
Trojan or attacked by a hacker and it starts sending your system information or
registration data thus lowering connection speed available for you or in any way
breaking your rights as a user of your PC (this is called computer fraud). If
you configure it with Anti-Hacker it will start working only in the area of FTP
Transferring thus disallowing virus activity (that's if your Anti-Virus didn't
detect the virus). Anti-virus should really cope with it. But what if this
happened in the Internet - with your Internet browser or something. It can
happen only in a few seconds or minutes and can be detected only by a major and
powerful Anti-virus system (not just one program but a set of powerful
anti-virus tools) and sometimes even not identified. That's when this rule
becomes really important.
Allow activity of application according to its type.
This rule allows application (you specify it's name) to work strictly according
to its type (you specify it's type). For example, you have a program 'A'
installed on your PC and it's an FTP Client. But somehow it's been infected by a
Trojan or attacked by a hacker and it starts sending your system information or
registration data thus lowering connection speed available for you or in any way
breaking your rights as a user of your PC (this is called computer fraud). If
you configure it with Anti-Hacker it will start working only in the area of FTP
Transferring thus disallowing virus activity (that's if your Anti-Virus didn't
detect the virus). Anti-virus should really cope with it. But what if this
happened in the Internet - with your Internet browser or something. It can
happen only in a few seconds or minutes and can be detected only by a major and
powerful Anti-virus system (not just one program but a set of powerful
anti-virus tools) and sometimes even not identified. That's when this rule
becomes really important.
![]() Disable all
activities of the application. This rule blocks (you can change it to
'allows' but it will turn this rule in the previous one, just described) the
application (you specify it's name) from any network activity. You use it for
the applications when you're sure they are infected or corrupted and/or mess up
your Internet access or system.
Disable all
activities of the application. This rule blocks (you can change it to
'allows' but it will turn this rule in the previous one, just described) the
application (you specify it's name) from any network activity. You use it for
the applications when you're sure they are infected or corrupted and/or mess up
your Internet access or system.
![]() Customize the
rule...This rule blocks (it's possible to change it to "allows") the
application access (you specify it's name) to establish connections [you can
choose from two types of connection sorted by the transferring direction: a)
establishing connection with remote machine or with your system's element; b)
receiving an incoming connection from either remote machine or your system's
element] to a remote computer/your system's element using the protocol TCP. So
here you configure the application from the different point of view: you
configure it by applying connection establishing rules. This is more neutral
option and is recommended for advanced users only because it provides advanced
control of the application, configuring any aspect of its activity.
Customize the
rule...This rule blocks (it's possible to change it to "allows") the
application access (you specify it's name) to establish connections [you can
choose from two types of connection sorted by the transferring direction: a)
establishing connection with remote machine or with your system's element; b)
receiving an incoming connection from either remote machine or your system's
element] to a remote computer/your system's element using the protocol TCP. So
here you configure the application from the different point of view: you
configure it by applying connection establishing rules. This is more neutral
option and is recommended for advanced users only because it provides advanced
control of the application, configuring any aspect of its activity.
3) Packet Filtering Rules
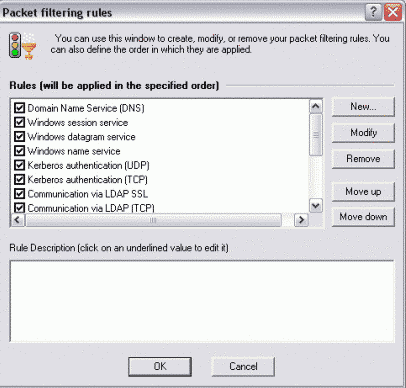
These rules have the same structure as the previous ones described but are applied not for applications, but services (I would call them systems of applications activities). These are different authentication systems, domain services (DNS etc.), communications via different protocols (UDP, TCP, SSL etc.) servers (BOOTP etc.), hosts etc. The same methods for configuring services and packet filtering are provided (I mean the same as for the previous rules category described):
It's possible to configure activity type of the service, 'allow' or 'block' commands for the rule, properties of the service. The following properties are usually provided: Packet Type (incoming or outgoing), Remote Address (can be entered using symbols - for example www.microsoft.com or using numbers - IP: 128.22.22.28 for example), Remote Port( POP3, SMTP, FTP or TELNET for example), Local Address (that's if the activity is for your PC - IP: 127.0.0.1 for example) and Local Port (that's if the activity is for your PC). I described 'Properties' menu only by categories. But there are more than one choice that can be set for each category (for example, for Remote or Host Addresses - subnet addresses or range of addresses etc.).
4) Security
I decided not to make illustrations of this option because it's actually quite easy-to-understand. It's just a system of logs (reports) of events happened in the areas of security, applications activity, packets filtering (services, authentication systems etc.). This may be useful if you forgot or somehow missed the rule that was set for a specific application, for example, or what happened to your system in the specific time. This is a standard component (Event Logging) that must be present in this type of programs (actually in any type now, in my opinion).
5) Active Network Applications
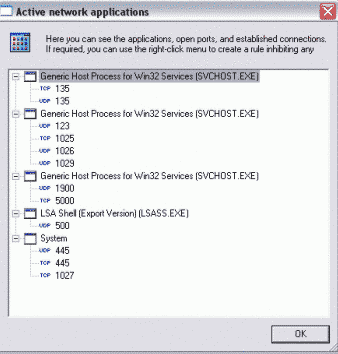
This option shows what network applications are working. This can be very useful when you don't know where the application is located so you can't set up a rule for it in 'Application Rules'. But using the right-click menu here you can create rules for active applications listed. This option also helps you to detect computer fraud. Because when you know something is going wrong with your computer at the specific moment you can quickly see Active Network Applications window and identify the application that causes the fraud.
6) Opened Network Ports
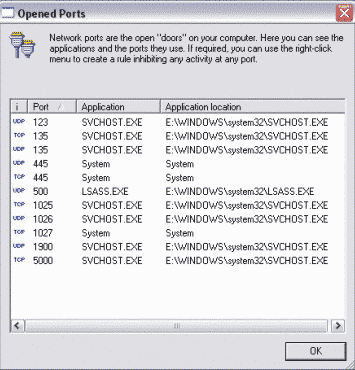
This option is an equivalent of the previous one for Network Ports. Here you can see ports that are active (opened) at the specific moment, applications they are being used by and their [applications'] location. You can set up rules for ports here. The purpose of this option is the same as of the previous one but is dealing with ports. Use this to detect computer frauds, create rules for ports in 'real-time' and other manual managing of ports of any kind.
7) Established Connections
I think no screenshot is required because this option is the same as two previous ones described in structure. The list of established connections allows you to identify applications communicating with remote ports. If required, you can break suspicious connections and create rules for them. This is another powerful tool for managing applications by established connections in 'real-time'. The option can be very useful for detecting computer frauds of remote kind.
8) Settings
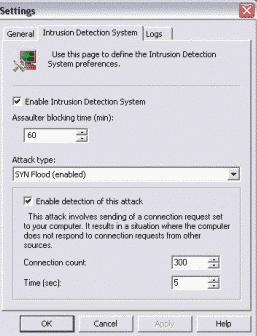
This menu is actually quite important. Except for general program options, 'Intrusion Detection System' options are offered. This system can also be called anti-hacker one. Here you can setup detection options for different types of attack as well as assaulter blocking time. You can enable/disable detection of SYN Flood, UDP Flood, ICMP Flood, Ping Of Death, Land, Scanning TCP Ports, Scanning UDP Ports attacks and enable/disable the whole Intrusion Detection System (IDS) at all. Finally, you can configure event logging in the 'Settings' menu.
![]()
This program is really advanced. Using it, you can get control of all applications' access to remote machines and your system. This is not just an anti-hacker software. Using it you can block unneeded and boring adware and any other kind of bots used to slow down your system in any way or just messing it up. If used together with a powerful antivirus (well, I would recommend Kaspersky AntiVirus - this is not an advert), your system is fully protected from any intrusions or frauds of all kinds.
![]()
![]() Kaspersky Anti-Hacker
v1.0.62.0 (9,2
MB, Shareware, Windows XP)
Kaspersky Anti-Hacker
v1.0.62.0 (9,2
MB, Shareware, Windows XP)
The software solution for the new product is available. Visit http://software-pc1.narod.ru .
P o s t e d o n 0 1 . 0 3 . 2 0 0 3 2 1 : 2 0 G M T
So enjoy the program. See you next week !!!! Peter L.
![]()
Tweak-XP Pro v2.0.8 -- HERE !!!
MagicTweak v2.20 -- HERE !!!
Kaspersky AV Personal Pro v4.0 -- HERE !!!
aTuner v1.3.9.4270 -- HERE !!!
ZoneAlarm Pro v3.5.169 -- HERE !!!
BadCopy Pro v3.60 build 1201 -- HERE !!!
FlashGet (JetCar) v1.4 -- HERE !!!
ReGet Deluxe v3.2 and 3.3 Beta -- HERE !!!
X-Setup v6.2 Final -- HERE !!!
Reg Organizer v1.39 and v1.4 -- HERE !!!
ACDSee v5.0.0.0025 -- HERE !!!
3DNA v1.0 -- HERE !!!
WinRAM Turbo XP v1.10 -- HERE !!!
Editorials
You can place banners of my site on your own site !!! Get them from below:
You can use up to 50% of materials placed on my site but only showing the source! Any mirroring of materials is prohibited !!! All these rules are followed by the LAW !!!